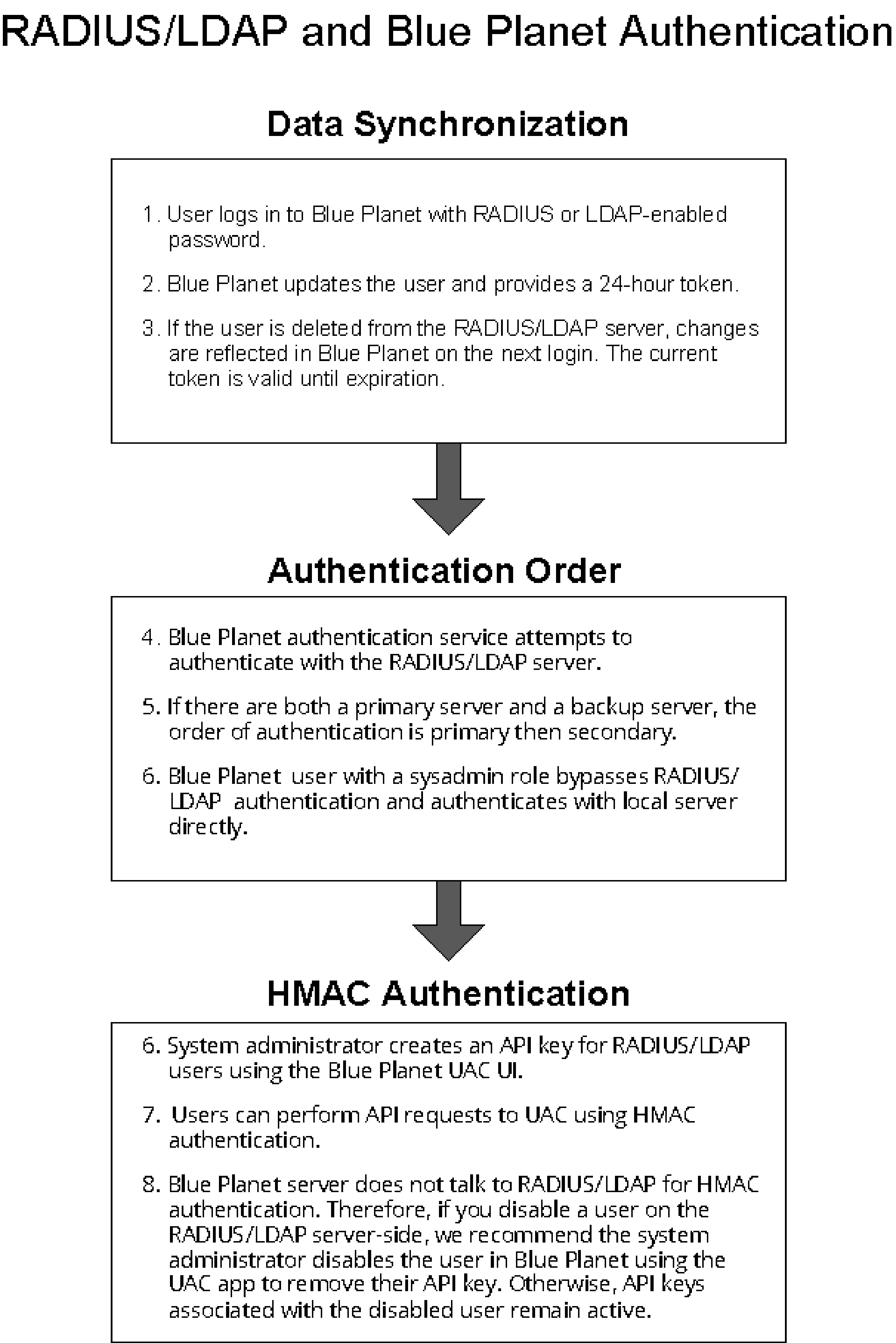
RADIUS/LDAP overview
The following diagram describes how RADIUS and LDAP authenticates its users in Blue Planet.

Important notes
Review these important notes before configuring RADIUS or LDAP on the Blue Planet server:
-
If a user logs in with Blue Planet UAC sysadmin privileges, authentication always succeeds, regardless if RADIUS/LDAP authentication is enabled or disabled.
-
Ensure the radius-config or ldap-configs name is either primary_config or backup_config.
-
Once RADIUS/LDAP is configured, you can authenticate to Blue Planet similar to a local user using RADIUS/LDAP credentials. In this release, you can configure RADIUS/LDAP for any tenant as long as you include the tenant name in the radius-config or ldap-configs definition. Use the same tenant name to authenticate users. If you do not include a tenant name, the system defaults to the master tenant. Blue Planet RADIUS authentication supports single tenants only in this release. LDAP authentication supports multi-tenants in this release.
-
With RADIUS or LDAP enabled, if you log in with your Blue Planet user credentials (and are not a privileged sysadmin), authentication fails.
-
To configure the LDAP role name feature to allow UAC to map LDAP role names to a specific role in a Blue Planet application, use the app. role_map JSON string. The string format is:
{"<LDAP_ROLE_NAME>": {"uac_role_name": "<ROLE_NAME_TO_MAP_TO>", "app_name": "<DISPLAY_NAME_OF_THE_APP>"}}. For example:`"roleMap":"{"Administrators": {"uac_role_name": "admin", "app_name": "UAC"}}"}RADIUS does not support the role_map feature.